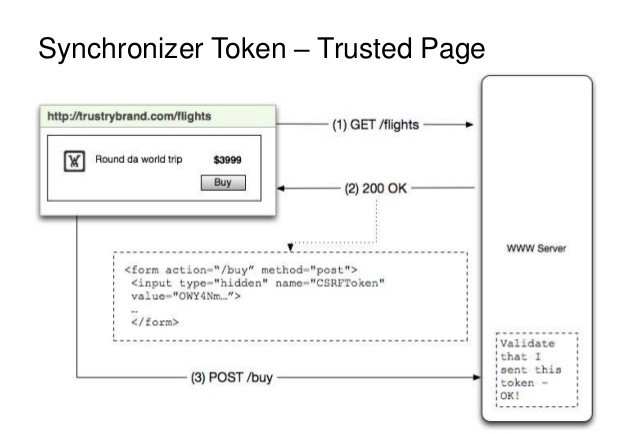
Cross Site Request Forgery Prevention - Synchronizer Token Pattern
With the Synchronizer Token approach, the server embeds a dynamic hidden variable in an input form. When the form is submitted, the server can check to make sure that the hidden variable is present and that it is the correct value.
In login.php, we have to generate a session identifier and set it as a cookie inside the web browser. At the same time it generates the “CSRF token” and saves it in the server side. The generated token is mapped to the session identifier.
In profile.php, You will see the form which you have to fill out a form providing your name, IT No and the faculty. What you can see is that there is a hidden field in this form which has the value of the received CSRF token.
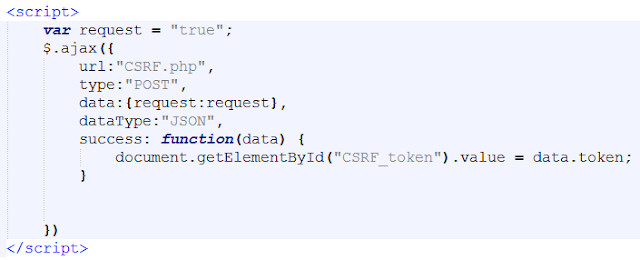
When this page loads, it executes an Ajax call which calls CSRF.php via a JavaScript which invokes the endpoint for obtaining the CSRF token created. What happens in the endpoint; which is submit.php in our case, it accepts the HTTP POST request and responds with the CSRF token.
Once this form is submitted, it extracts the received token value and check whether if its the correct token issued for the particular session. If Yes it will successfully display your user profile details you entered. If not it will display you an error message.
The output is like this.
Source code : CSRF Protection - Synchronizer Token Pattern












Comments
Post a Comment